Verkada intercoms setup guide v1, Verkada’s intercom solution enables you to answer calls, grant entry, and secure entrances from anywhere.
Get Started with Verkada Intercom Set up and connect your Verkada intercoms Updated over a week ago
Required. You need Org Admin and/or Site Admin permissions for your Verkada Command organization to complete these actions.
What you need
Create a site
Sites are the logical way of grouping and managing devices within your Command organization. Site-level permissions make managing and viewing your devices easier. See Manage Your Sites and Subsites for more information on site creation and management.
Add an intercom
At least one intercom needs to be added to Command before you can see the Intercom tab in the All Products menu. Intercoms can be added to Command from the Devices page. See Add an Intercom to Your Site for more information.
Connect a door
You can pair an existing access-controlled door or wire a door to the intercom that can be unlocked by an intercom receiver. See Configure a TD52 and Wire a TD52 Video Intercom for more information.
Configure receivers
Receivers allow you to answer calls from an intercom and unlock any associated doors. See Add and Configure Receivers in Intercom for more information.
Licensing
Every intercom you manage in Command will need a license. Verkada licensing is applied for each Command organization, and the licenses co-term to a single expiration date. Your licenses may have been automatically added if you claimed your devices via order number. Otherwise, manually add the licenses from the Admin page. See Manage Your Licenses for more information on adding and managing licenses.
Connect your intercom
Recommendation. While Verkada intercoms are considered low-voltage devices that do not require a certified electrician to install, we strongly recommend you work with a system integrator or other professional for installation.
Please refer to the intercom setup guide for instructions on mounting and wiring the door port.
Power and network
Verkada intercoms use Power over Ethernet (PoE) for power and communication over the LAN. In most cases, intercoms will connect directly to an 802.3af PoE standard switch. PoE injectors can be used when a PoE switch is not available. See the intercom’s datasheet for more information.
Check network settings
Verkada intercoms are designed to be plug-and-play. However, if your environment includes a firewall with custom rules and policies, you may need to make some configuration changes to get your access controllers connected to the cloud. See Intercom Network Settings for more information.
Roles and Permissions for Intercom
Roles and Permissions for Intercom
Learn more about Verkada Intercom roles and permissions
Updated over a week ago
This article describes the set of roles and associated permissions for Verkada Intercom.
See Roles and Permissions for Command users for an in-depth explanation of the features and configurations available for overall Verkada Command usage and administration.
Verkada intercoms setup guide v1
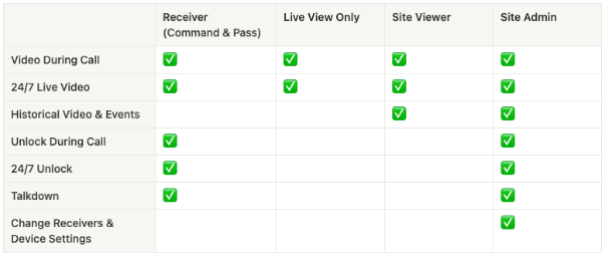
Verkada Intercom permissions determine who can receive calls, view intercom video, and unlock intercom doors. Intercom permissions depend on your site-level permissions, and whether you’re configured as a Receiver.
At a high level, these are the permissions granted to each level of Intercom devices:
Site-level roles
Receiver
Required. You must be configured as a receiver to receive calls.
If you’re a Verkada Intercom Receiver, you have the baseline receiver permissions (as shown above). These baseline Receiver permissions combine with site-level permissions to determine overall intercom permissions within a certain site.
For example, if you’re a Receiver for a particular intercom, and a Site Viewer, you get all the Receiver permissions, in addition to the ability to view historical video and events.
Note: Receivers, such as Desk Stations and Session Initiation Protocol (SIP) phones are not tied to a Verkada Command user. This means that the user can only get Receiver permissions, regardless of the user’s site-level permissions.
Regardless of their site-level permissions, a Receiver can:
Live-View Only
Site Viewer
Site Admin
.
Verify a user’s eligibility to receive Verkada Pass calls
.
Set Org Admin permissions
Revoke Org Admin permissions
.
Set site and subsite permissions
You can set site and subsite permissions by adding a user, a group, or by existing users and groups.
Add a user
Add a group
Existing users and groups
You can set the site and subsite permissions for existing users and groups by managing the user roles or the sites.
Manage roles
Manage sites
Intercom Network Settings
Intercom Network Settings
Learn about the required network settings for Verkada Intercoms
Updated over a week ago
This article outlines the required network settings that your Verkada Intercom needs to communicate with Verkada Command. For more information on the required network settings for other Verkada product lines see Required Network Settings.
Note: Verkada devices are incompatible with LANs that require proxy servers or Secure Socket Layer (SSL)/Transport Layer Security (TLS) inspection. If either is in use, a bypass for all Verkada devices must be implemented for Verkada devices to communicate with Verkada Command.
Status LED
A flashing blue status LED on the top of the intercom indicates the intercom is not communicating with Command. If you see this behavior, check that the network is set up correctly with the intercom’s requirements. If the problem persists, contact Verkada Support.
IP address
Intercoms must be assigned an IPv4 address to communicate on the LAN and to Verkada Command. Intercoms use Dynamic Host Configuration Protocol (DHCP) and User Datagram Protocol (UDP) to obtain their IP addresses and network configurations.
If you require your intercom to have a specific IP address, create a DHCP reservation using the device’s Media Access Control (MAC) address (found on the device’s label).
Domain Name System
Intercoms use the DNS server to resolve Verkada’s fully qualified domain names (FQDN) to IP addresses to communicate with them. Your DHCP server tells the intercom where the DNS server is on the network and the intercom communicates using UDP port 53.
Note: DNS over HTTPS (DoH) is currently not supported.
Power
Intercoms are powered through Power over Ethernet (PoE). This means the network switch needs to provide power to the intercom, or a PoE injector needs to be utilized. For specifics on power requirements, see the Intercom datasheet.
Firewall settings
Intercoms require access to many endpoints to ensure they can communicate with Command and all features will be accessible. Many customers may want to allow the intercoms to communicate with the general required endpoints.
These are the general domains to allow, applicable for all organization-regions:
If your firewall does not allow wildcard masking, or you prefer to have the entire FQDN of the endpoint in your firewall rules, you can add the domains to your allowlist based on the region your devices are in.
Note: Your region is selected when you create an organization in Command.
Region: United States
Standard Verkada Endpoints
NTP Endpoints
Streaming Endpoints
Calling Endpoints
Access Control Endpoints
Cloud Backup Endpoints
Region: Europe
Standard Verkada Endpoints
NTP Endpoints
Streaming Endpoints
Calling Endpoints
Access Control Endpoints
Cloud Backup Endpoints
Footnotes:
†required for Desk Stations and Verkada Pass
‡required for cloud backup
Mount a TD52
Mount a TD52
Learn how to mount the Verkada TD52 Video Intercom
Updated over a week ago
Use this article to learn how to mount a Verkada Intercom (TD52). Once you complete the mounting, you can connect the TD52 to the network.
Before you begin
You can mount the TD52 using a flush mount or using a mounting bracket. We recommend that you verify the contents of your box and make sure you have the tools you need
Contents of your box
Tools you need
Choose your mounting option
Whichever mounting option you choose, you should remove the front cover of the TD52 to access the screw holes that allow you to install on a mount.
Use a flush mount
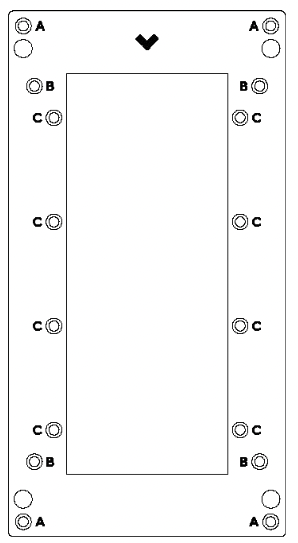
The TD52 comes with a flush mount in the box. You can use the screw holes of the flush mount to mount the Intercom (see image below for visual):
Mount directly to a wall
Use a mounting bracket
You can use the mounting bracket to install the TD52 on to various surfaces that the flush mount plate cannot, where they’re typically used to mount the TD52 on an exterior surface.